Table of Contents
- What should I read?
- What’s your risk level?
- Open source and encryption are your friends
- Quick start in 50 minutes
- Privacy basics in 90 minutes
- End-to-end encryption for your data in 4 hours
- Reclaim your bubbles of freedom
- Appendix: I care about digital privacy a lot
- Appendix: A prescient, under-heeded warning about ice in 2022
- Footnotes
By George Retes, Iraq war veteran
My wallet with my identification was in the car, but the agents refused to go look and confirm that I was a citizen. Instead, I sat in the dirt with my hands zip-tied with other detainees for four hours. When I was sitting there, I could hear agents asking each other why I had been arrested. They were unsure, but I was taken away and thrown in a jail cell anyway.
My first night in jail, my hands were burning from the pepper spray and tear gas because I was never allowed to wash them off. During the three nights and three days I was locked up and put on suicide watch, I could not make a phone call and was not given a chance to speak to a lawyer.1
George’s story isn’t an isolated incident. ProPublica found that “more than 170 US citizens have been held by immigration agents. They’ve been kicked, dragged and detained for days.” As of October 2025, ice has become a lawless, unaccountable agency—a starving, rabid dog let off its leash. Generally, rabid dogs are not empowered by the full force of the US federal government. This one is. That same government has declared its political opponents to be “domestic extremists” and pursues a naked agenda of persecution.
Authoritarianism is here. Protect yourself.The Trump regime views its political opponents as literal enemies of the state:
Trump’s Deputy Chief of Staff for Policy and Homeland Security Advisor
The Democrat Party does not fight for, care about, or represent American citizens. It is an entity devoted exclusively to the defense of hardened criminals, gangbangers, and illegal alien killers and terrorists. The Democrat Party is not a political party. It is a domestic extremist organization.
Trump signed an executive order designating “antifa” as a “domestic terrorist organization” (not a legal classification, and “antifa” is not a specific organization). Days later, Trump issued National Security Presidential Memorandum 7 on “Countering Domestic Terrorism”, which directs federal agencies to prioritize investigations of ideologies under “the umbrella of self-described ‘anti-fascism.’” These ideologies include “anti-Americanism, anti-capitalism, and anti-Christianity; support for the overthrow of the United States Government; extremism on migration, race, and gender; and hostility towards those who hold traditional American views on family, religion, and morality.”
The order put the fbi’s Joint Terrorism Task Force in the lead and directed the Treasury Department “to identify and disrupt financial networks that fund domestic terrorism and political violence”, naming Democratic donors George Soros and Reid Hoffman as potential targets (without providing evidence).
This is going to be a big thing for the people in this room, because it’s the enemy from within, and we have to handle it before it gets out of control. It won’t get out of control once you’re involved at all. We’re under invasion from within. No different than a foreign enemy, but more difficult in many ways because they don’t wear uniforms.
In our inner cities—which we’re going to be talking about because it’s a big part of war now. It’s a big part of war. San Francisco, Chicago, New York, Los Angeles. They’re very unsafe places. And we’re gonna straighten them out one-by-one. This is gonna be a major part for some of the people in this room. It’s a war, too.
It’s a war from within.
On October 8th, 2025, Trump posted that Chicago Mayor Brandon Johnson and Illinois Governor JB Pritzker “should be in jail for failing to protect Ice Officers!”. When pressed by reporters about what crimes he believed they had committed, Trump said “I’ve seen the law” and doubled down on his call for their imprisonment.
Trump labels his opposition as terrorists, targets political ideologies through executive orders, and tells America’s generals to prepare to go to war inside our own country. Sooner or later, you might become an “enemy from within.”
Accept the reality of the risk cast by the future. Act now to prepare.
This guide will help you protect your communications and information so you can think and speak freely. The privacy won’t be perfect, but it should give you breathing room. As more people reclaim their privacy, their networks grow more secure and resistant to authoritarian punishment.
Let’s get started.
I’m only speaking for myselfMy day job is AI alignment research at Google DeepMind. I’m only expressing my own views. This guide synthesizes research from security experts and represents my personal practices.
This guide is long. Don’t try to complete it all at once. My website has long-lasting checkbox functionality. As you complete items, check them off to remember your place in the guide.
This guide is freeIn the following table, I estimate the cost of purchasing the equipment and services recommended in the different tiers of the guide.
| Tier | Time for tier | Anticipated cost of tier | Protection level |
|---|---|---|---|
| Quick start | 50 minutes | $0 | Online accounts secured against most hacking. Limited private communication ability. |
| Privacy basics | 90 minutes upfront + 45 minutes for YubiKey setup when it arrives | $110 + $13 / month | Significant privacy against mass surveillance. Govt. has a harder time seeing who you talk to and can’t easily monitor what you say on the Signal app. |
| End-to-end encrypt your data | At least 4.5 hours | $14 / month | Mass surveillance unlikely to capture your important data or communications. |

Each tier builds on the previous, so do them in order.
- Something is better than nothing. Even a few hours can transform your privacy.
- If money is hard to come by, don’t worry—many of the best interventions are free.
- If you find this subject distressing, you’re not alone because I do as well. Do what you can.
By Bruce Schneier, famous cybersecurity expert
Being innocent won’t protect you.
This is vital to understand. Surveillance systems and sorting algorithms make mistakes. This is apparent in the fact that we are routinely served advertisements for products that don’t interest us at all. Those mistakes are relatively harmless—who cares about a poorly targeted ad?—but a similar mistake at an immigration hearing can get someone deported.
An authoritarian government doesn’t care. Mistakes are a feature and not a bug of authoritarian surveillance. If ice targets only people it can go after legally, then everyone knows whether or not they need to fear ice. If ice occasionally makes mistakes by arresting Americans and deporting innocents, then everyone has to fear it. This is by design.
| Your situation | Threat level | Recommended sections |
|---|---|---|
| Living in a stable democracy, a Trump supporter who does not belong to any marginalized groups | Low | Quick Start & Privacy Basics |
| US citizen who does not support Trump | Medium | This guide and the sequel, all sections |
| Immigrant, journalist critical of regime, opposition politician | High | Both guides & consult security professionals |
| Facing imminent arrest or deportation | Critical | This guide is insufficient—seek legal counsel immediately |
This guide is about protecting yourself, but it’s not necessarily about hiding. I personally think what’s going on right now is horrible and that most citizens should act. At the same time, you should take intelligent risks via intentional public statements—not avoidable risk because the government spies on your private communications.
Not sufficient for people at high risk of targeted surveillanceIf you’re at risk, read this guide and the more advanced sequel but also refer to a more hardcore guide with targeted surveillance in mind and consult a security professional.
What information this guide will and won’t help you protectIf your phone is connected, cell towers track your approximate location. License plate readers track your car. Facial recognition identifies you in public spaces and others’ photos. You will be hard-pressed to turn invisible while participating in modern society.
This guide will teach you to protect a limited selection of your data:
- Content of your communications (Signal e2ee),
- What you’re researching and reading (vpn hides websites),
- Your organizing documents and plans (e2ee cloud storage),
- Your network and contacts (e2ee contact storage),
- Correlation across identities (pseudonymity, email aliases).
In high-risk situations, leave wireless-enabled devices at home, in airplane mode, or in Faraday bags for truly sensitive meetings. Otherwise, pessimistically assume the government knows where you are at all times. Also, financial privacy is hard and this guide only helps a bit on that front.
This article will assume less computer science background than most of my articles do, and that’s because I’m writing for friends and family. I’ll give concrete, specific, and immediately actionable recommendations. For example, no decision paralysis from waffle-y lists of the “top 10” password managers. I’ll tell you what to use.
I’ve structured my recommendations around two key principles.
- Open source code
- If a program is open source, then that means anyone can see its code. In turn, that means if the developers put something suspicious or sneaky in the program, someone will probably read the code and notice. You don’t need to trust that the people who made the app didn’t include creepy tracking.
-
Open source programs are usually free as well!
- End-to-end encryption (e2ee)
- While Apple Calendar might encrypt the events you schedule, that’ll only prevent outside people from taking a peek. If Apple wanted to, they could look at your calendar. More concerningly and more likely, if a government demands that Apple hand over your schedule, they’re able to and need to comply. However, if you enable end-to-end encryption, that’s no longer possible, because only you can unlock or decrypt that information.
-
Pessimistically, you should assume that anything which isn’t e2ee can be read by the government.
Unless I mention otherwise, all of my recommendations are both open source and e2ee. By following this guide’s recommendations, you will create “dark spots” where the surveillance apparatus has trouble looking. Even in the face of an authoritarian crackdown on thoughtcrime, you will have space in which to think freely and to organize discreetly.
Time: 30 minutes with ongoing maintenance as you import passwords.
Use a different long password for every single login you have. Do not reuse passwords. Do not reuse passwords. Do not make simple passwords like mail123.
If you’re not using a password manager already, Bitwarden will make your life easier. Bitwarden will remember your passwords and logins for you. It can even fill them in automatically. Bitwarden will generate new secure passwords for you. Never again must you worry, “which password did I use for this website?!”. You just remember one password: the master password for Bitwarden.
Here’s what to do:
Since you’re using a unique password for every site, you won’t have to scramble in the event of a breach. The only account which might even possibly be compromised is the specific account whose password was breached. After all, the compromised password has nothing to do with all the other passwords which Bitwarden generated!
Bitwarden (the company) cannot access any of your information or passwords—only you can.
“2-factor authentication” means an attacker has to try a lot harder to get into your accounts, because they need a password and another piece of information—a second “factor.” Even if your credentials are exposed in a massive breach, your account will be safe because they won’t have access to your second factor.
Enable two-factor authentication on every possible account that you care about protecting. You don’t have to do it all at once. You can just enable 2fa on your most important accounts and then start enabling them in the future as you notice.
The US government forces telecoms to permit spying on their customers (including you). Assume that all text messages and phone calls are actively monitored by the government.
The Act obliges telecommunications companies to make it possible for law enforcement agencies to tap any phone conversations carried out over its networks, as well as making call detail records available. The act stipulates that it must not be possible for a person to detect that his or her conversation is being monitored by the respective government agency.
[…] Journalists and technologists have characterized the calea-mandated infrastructure as government backdoors. In 2024, the U.S. government realized that China had been tapping communications in the U.S. using that infrastructure for months, or perhaps longer.
Since the American government mandated vulnerabilities in key American communications infrastructure, the Chinese government was also able to exploit those vulnerabilities.
What is clear is sms is not acceptable, even for temporary, one-time passcodes. “Do not use sms as a second factor for authentication. Sms messages are not encrypted—a threat actor with access to a telecommunication provider’s network who intercepts these messages can read them. Sms mfa is not phishing-resistant and is therefore not strong authentication for accounts of highly targeted individuals.”
Time: 5 minutes to install app.
The fast and free upgrade is to prefer authenticator apps over sms and email.
As far as applications go, common apps store your 2fa secrets in the cloud without e2ee, which means the cloud owners could theoretically see which websites I’m authenticating with. Proton Authenticator is the answer.
Make sure you’ve enabled automatic security updates on your device. Just search “security update” in your phone and computer settings. Enable automatic updates for both. Install operating system updates asap.
If you use iCloud, enable adp. In a single flick, adp will enable end-to-end encryption (e2ee) for the vast majority of the data you store in iCloud. The exceptions are Calendar, Contacts, and Mail. I’ll cover how to encrypt those later. Also, even for e2ee content, Apple retains limited metadata (like filename and size).
WarningIf you are in the UK, you may have to refer to the later section on achieving e2ee for your data. That’s because Apple stopped supporting adp for new UK users after being pressured by the UK government. It’s as tale as old as
<time.h>: degrading the freedom and privacy of the Web, extending government surveillance—all in order to “protect the children.”
Use an eight digit pin for your phone. Using Bitwarden, secure your laptop with a passphrase which consists of five randomly generated words. After a couple tries, you’ll remember it.
On Mac, I just hit ctrl+command+Q by habit. Otherwise, someone in the area could walk by and browse. Constant vigilance!
Time: 5 minutes.
Plain phone calls and text messages are not encrypted. That’s why the government has been warrantlessly spying on them for a long time. “Encrypted” services (which aren’t e2ee) aren’t that safe either:
Digital services like Facebook Messenger, Telegram, or X may say their direct messages offer “encryption”, but in the default setting that almost everyone uses, they only encrypt information in transit to the server that runs the service. On that server, the information is then decrypted and accessible to the company that controls that server, or any government agency that demands they share that data—like the Nebraska police who demanded Facebook hand over chats about a 17-year-old’s illegal abortion in 2022, then brought criminal charges against her and her mother.
The well-known application Signal is both open source and e2ee. Secure your communications. Use it.
Consider encouraging your friends to use Signal.I don’t really use other texting applications anymore.
Cost: Free, with recommended upgrade at $13.99 / mo. Time: 15 minutes.
When you browse the internet, you send your isp a list of sites you’re browsing. They usually can’t see the data you’re receiving, but they still see where you’re going and who you are. When you use a vpn, isps can no longer see that information.
The new ftc report studied the privacy practices of six unnamed broadband isps and their advertising arms, and found that the companies routinely collect an ocean of consumer location, browsing, and behavioral data. They then share this data with dodgy middlemen via elaborate business arrangements that often aren’t adequately disclosed to broadband consumers.
“Even though several of the isps promise not to sell consumers personal data, they allow it to be used, transferred, and monetized by others and hide disclosures about such practices in fine print of their privacy policies”, the ftc report said.
US government spy agencies have broad surveillance powers which allow them to compel isps and other service providers to hand over communications data without a warrant. While https encryption (used by most major sites) prevents isps from seeing the specific parts of the site you visit or what data you send, they can still see:
- Which domains you visit (e.g.
google.com), - When and how often you visit them,
- How long you spend on each site, and
- Your full browsing activity on the sites that still don’t use https.
The metadata alone reveal a detailed picture of your online life. A vpn prevents your isp from seeing this information, since all your traffic is encrypted before it reaches the isp.
I recommend downloading Proton vpn. While Proton vpn has a generous free version and is probably the best free vpn there is, it’s still the free version. I found the download speed to be slow and unreliable. When I upgraded to the paid version, my problems vanished. Personally, I recommend purchasing a subscription to Proton Unlimited ($12.99 / month, or $9.99 / month if you pay for one year at a time). That subscription will not only unlock the paid vpn tier but will also provide 500gb of e2ee storage via Proton Drive.
The isp won’t see which sites you browse, but Proton willTo connect to the internet, some server needs to figure out where your internet traffic should go. When you don’t use a vpn, your isp handles that. When you do use a vpn, the vpn provider does instead. Therefore, Proton can see what sites you visit.
So why use Proton vpn? Several reasons. Most importantly, your isp will generally record your activity and funnel it to the government. In contrast, Proton doesn’t record your activity, as verified by independent experts.
Does Proton vpn keep logs?In order to respect our users’ privacy, Proton vpn enforces a strict no-logs policy. This means we keep no session usage logs of what you do online, and we do not log metadata that can compromise your privacy.
- We don’t log which websites you visit
- We don’t log your traffic or the content of any communications
- We don’t log your IP address
- We don’t log your session lengths
- We don’t log or track any location-based information
This level of privacy is possible in part because we are based in Switzerland, which has some of the strongest data protection and digital privacy laws in the world. Data required for maintenance and troubleshooting purposes is secured using full-disk encryption on all our bare-metal servers, over which we have full control.
Full details about the information that we do store (such as account information) are available in our Privacy Policy. Our apps are all fully open source and independently audited so that you can be sure they are trustworthy, and we aim for transparency in everything we do.
Proton vpn’s Swiss jurisdiction also confers additional benefits which are favorable for vpn services. In most countries, vpns can be forced to log as the result of government orders, even if they are by default no-logs. However, within the current Swiss legal framework, Proton vpn also does not have forced logging obligations.
[…]
Proton vpn’s strict no-logs policy was tested in a legal case in 2019 where we were ordered to turn over logs to help identify a user and we were unable to comply because such logs did not exist. Our no-logs policy has also been verified by external independent experts.
As discussed later in the section on securing your data with end-to-end encryption, Proton applications are open source, e2ee, and well-respected in privacy circles. For example, using Proton Calendar (e2ee) instead of iCloud Calendar (a government could compel Apple to decrypt your data, even though Apple secures your data quite well).
- In the settings, ensure:
For network stability and speed, I strongly recommend upgrading to Proton Unlimited for $12.99 / month. I recommend several Proton services, including Proton Mail and Drive. Once you upgrade, enable “vpn accelerator” in the settings.
Some websites may think you’re a bot because many people use the same vpn ip addressCompared to other vpns, I’ve heard that Proton vpn is relatively good about not getting you flagged. Sadly, I still get flagged a few times a day, which is inconvenient but worth the privacy boost.
Consider changing vpn servers in the app when you run into problems. For non-sensitive tasks, you can even disable the vpn—but please do so sparingly (do not make a bad habit). Your vpn is your most powerful shield against mass surveillance.
DangerI was ready to wrap up writing when I found out some intricately bad news: vpns on iOS will often “leak” and expose your browsing habits to your isp. iOS system services sometimes ignore your vpn entirely. This ruins your protection from surveillance by exposing your browsing history directly to Internet Service Providers (aka us spying data collection points). Apple states that ignoring your vpn is “expected behavior.” After five years of known vulnerability, no fix is available for consumers.
macOS has a similar problem. The only reliable workaround is to always connect to a router which enforces vpn protection for all of its traffic (covered in the sequel post).
Should you still use a vpn on an Apple device? Yes—it’s still better than nothing. Know that the isp (and Apple) will see some metadata.
The Android situation is better. Sadly, there are rare circumstances where vpns won’t protect your traffic. Android apps can leak past the vpn when they otherwise can’t connect. Android also sporadically makes Wi-Fi “can I connect?” checks which ignore your vpn, which isn’t great—but that leaks far less information. All in all, it seems like Android is better in terms of vpns.
Even vpn-protected browsing theoretically enables AI to guess which sites you visitAs of October 2025, I only found one vpn with meaningful protection: Mullvad. However, it’s based in Sweden, a member of the 14 Eyes intelligence-sharing alliance with the United States. That undermines protection from US surveillance. I suggest sticking with Proton vpn.
Here are several reasons for comfort:
- The attacks seem too expensive to run as mass surveillance, and
- Many attacks only allow determining whether or not you’re visiting one of a tiny number of sites.
I wouldn’t worry about this too much for now. Hopefully Proton implements a defense, just to be sure.
It’s not paranoia if they really are out to get youUnder Section 702 of the Foreign Intelligence Surveillance Act, the U.S. government engages in mass, warrantless surveillance of Americans’ and foreigners’ phone calls, text messages, emails, and other electronic communications. Information collected under the law without a warrant can be used to prosecute and imprison people, even for crimes that have nothing to do with national security. Given our nation’s history of abusing its surveillance authorities, and the secrecy surrounding the program, we should be concerned that Section 702 is and will be used to disproportionately target disfavored groups, whether minority communities, political activists, or even journalists.
In late 2024, the government further expanded its surveillance powers.
June 5th, 2024
Under the newly enacted “spy draft” provision, the government can not only enlist telecom providers like Verizon to hand over information about their subscribers’ contacts with foreigners it is investigating, as it has in the past. It can conscript any American service provider to spy on its behalf. Senator Ron Wyden noted that cleaning services could be compelled to insert a usb thumb drive into a server at an office they clean.
Time: 30 minutes.
I thoroughly ran available browsers against my criteria for you:
- Strong privacy protection against commercial and governmental tracking,
- Strong ad blocking,
- Runs websites smoothly without major usability sacrifices,
- E2ee history and preferences sync across mobile and desktop,
- Open source, and
- Good default settings (convenient for you).
I settled on Brave, based on Chromium. The browser is a huge privacy upgrade from normal browsers, especially in the context of recent restrictions on popular ad blockers. I also found it straightforward to migrate to Brave.
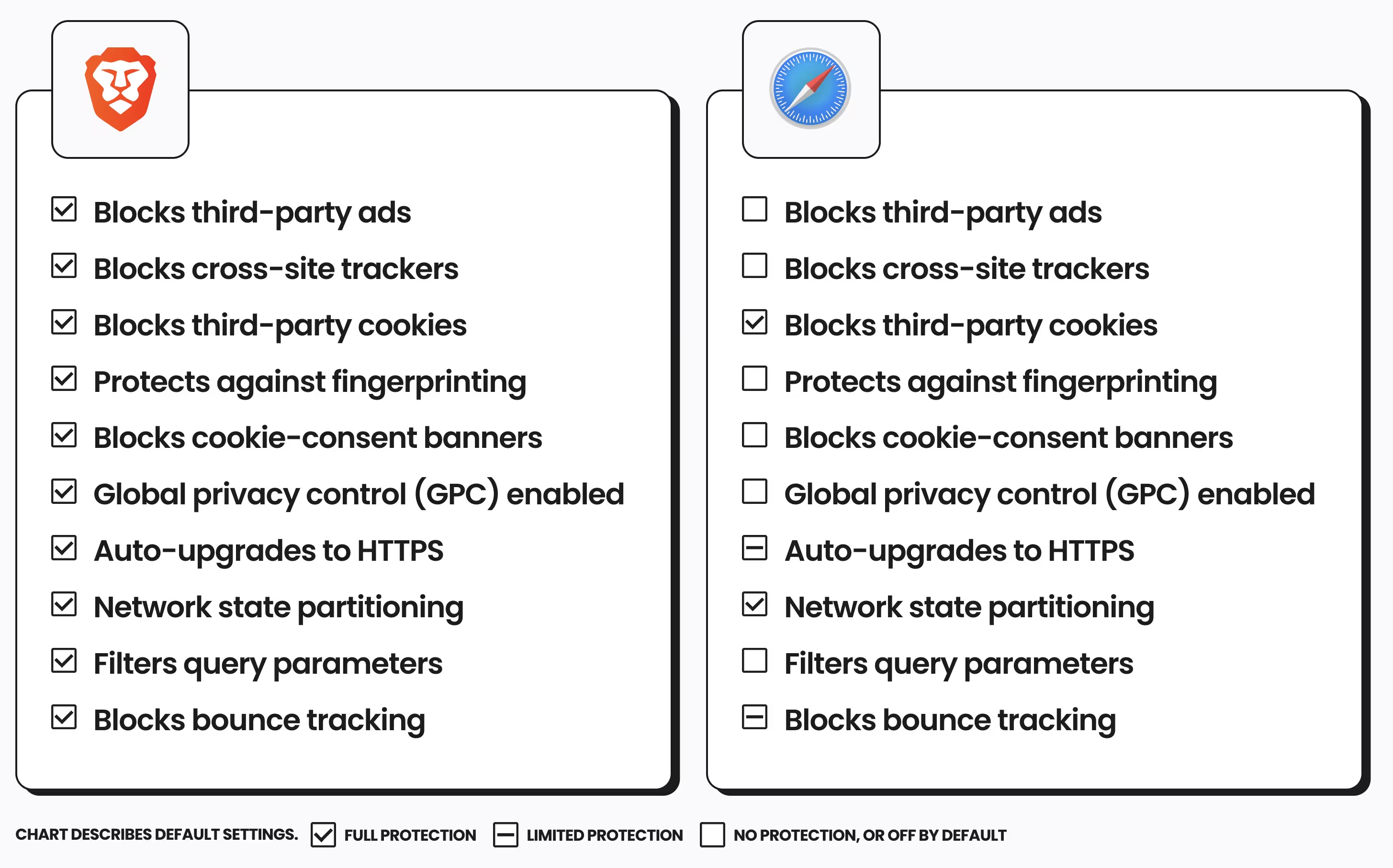
privacytests.org.Brave’s company has made a few shady moves in the past. But Brave is the only browser which met my six criteria. In terms of privacy, Brave is far better out of the box than its competitors. Your account information and browsing history is e2ee, meaning you don’t have to trust the company itself. Even if you don’t like some of the actions taken by the company, you don’t have to pay anything to use the browser. You don’t have to trust them that the code is secure because people can just look at that code.
If you don’t want to use Brave, I recommend hardening Firefox using Arkenfox (requires technical expertise) or using the Firefox fork Librewolf (which deletes your cookies and history each setting, disrupting your usual usage patterns).
Optional additional protections to apply
Send your friends clean linksYou ever see those suuuuper long urls and think, wtf? Generally, those urls are full of trackers saying things like “this user came from a specific Facebook ad, has this browser version, and lives near this city.” Brave cleans those links in your own browsing experience. But if you’re copying a link and notice that kind of url, go back, right-click the link, and select “copy clean link.” Brave will strip away that information.
Insight: reducing commercial tracking reduces your exposure to government trackingCompanies track you and sell your data. Then the US government buys your data.
Mobilewalla does not collect the data itself, but rather buys it from a variety of sources, including advertisers, data brokers, and internet service providers. Once it has it, the company uses artificial intelligence to turn a stew of location data, device IDs, and browser histories to predict a person’s demographics—including race, age, gender, zip code, or personal interests. Mobilewalla sells aggregated versions of that stuff back to advertisers. On its website, Mobilewalla says that it works with companies across a variety of industries—like retail, dining, telecom, banking, consulting, health, and on-demand services (like ride-hailing).
“… an enormous number of Americans—probably without even knowing it—are handing over their full location history to shady location data brokers with zero restrictions on what companies can do with it”, Warren said. “In an end-run around the Constitution’s limits on government surveillance, these companies can even sell this data to the government, which can use it for law and immigration enforcement. That’s why I’ve opened an investigation into the government contracts held by location data brokers, and I’ll keep pushing for answers.”
Time: 2 minutes.
Brave is much better for our high privacy needs. However, Brave is not as good as Google at surfacing the desired result. If you don’t get what you want the first time, consider sending it over to Google by beginning your query with !g.
Time: 20 minutes to review existing permission settings.
Be especially wary about giving out precise location data. Don’t be afraid to say “no” if a permissions request seems unreasonable—you can always read more on the app and come back later if you change your mind. Review your mobile and desktop applications in your permissions centers. Check that apps aren’t taking absurd permissions they don’t need (like a calculator asking for access to contacts).
Minimizing location permissionsI found several apps were using my location all of the time, including:
- My Govee smart lights app (deny!),
- Maps (should only need it when I’m using the app), and
- System Intelligence (doesn’t need much location data).
Time: 5 minutes to order & 40 minutes to secure your most important accounts. Cost: $110.
YubiKeys are physical devices which guarantee “these accounts cannot get hacked remotely.” They constitute the strongest form of 2fa. To log into an account protected by your YubiKey, you physically tap the key. Accounts like your email or Bitwarden are extremely valuable and worth protecting. The security ordering is: YubiKey > authenticator app > text- / email-based 2fa.

You buy two of these little usb-c boys for $55 each. Use these as two-factor authentication for your most sensitive accounts. You really, really don’t want hackers to compromise your Bitwarden.
- Buy two keys.
- Set up key-based 2fa on your most important logins. For each site, register 2fa on both keys.
- Keep the two-factor key in your laptop case or on a keyring. Put the other in a secure location protected from fire and flooding. You could put it in a bank deposit box or in a private safe at home.
These keys are expensive. Do I really need two?I know they aren’t cheap. Software 2fa is pretty good, too. However, hardware keys make you basically immune to being remotely hacked on your most important accounts (though someone could still do it if they were physically present). That immunity brings security but also peace of mind. To check which services accept YubiKeys before you buy, check out the 2fa directory. Since you’re at least using Bitwarden, I think hardware keys are still worth it unless you’re on a tight budget.
At minimum, you need two keys. If you just had one key, you’re one “oops I lost it” away from being locked out of your most important accounts. Scary! By keeping a backup safe and sound, even your home burning down shouldn’t destroy both of your keys.
For convenience, you might even get a third key: a YubiKey 5C Nano (an additional $65) which you always leave plugged into one of your computer’s usb-c ports. This can’t be your main key because you’d be unable to access your accounts on mobile unless you always have your computer with you (and thus the Nano as well).
Time: 2 minutes.
Every time you take a picture or video with your phone, your phone tags the media with your location. So if you upload a picture, you’re saying where you were. If an adversary gains access to a sequence of images you’ve shared, they’ll probably know where you go on a daily basis. (However, when you send media using Signal or Proton Mail, the application will scrub the location metadata.)
Stop your phone’s camera from saving this automatically. Reduce the number of ways you unknowingly leak location information.
- Android
- Search “geotag” in your settings, or just find the setting in your Camera settings.
- iPhone
- Settings ⭢ Privacy ⭢ Location Services ⭢ Camera and select “Never.”
Your files contain more metadata than just locationYour photos also might expose what kind of phone you’re using and the time you took the photo. To remove these from extra-sensitive images, use a special application. Example: Play Store, App Store.
If it’s on the cloud and not e2ee, assume the government can read it.
Not only does the Government have the power to issue secret subpoenas demanding your personal information from private companies—it has the power to prohibit those companies from speaking about what has taken place.
It doesn’t matter how good a company’s security and data handling practices are. Google and Apple have amazing security. If a company can decrypt your data, the government can force the company to decrypt your data. It’s not the company’s fault—they would just have to comply.
The Clarifying Overseas Use of Data (cloud) Act… creates an explicit provision for U.S. law enforcement (from a local police department to federal agents in ice) to access “the contents of a wire or electronic communication and any record or other information” about a person regardless of where they live or where that information is located on the globe. In other words, U.S. police could compel a service provider—like Google, Facebook, or Snapchat—to hand over a user’s content and metadata, even if it is stored in a foreign country, without following that foreign country’s privacy laws.
On the other hand, when you use e2ee, the company can’t decrypt it. Your data is just a sequence of zeros and ones on a computer. The company has nothing to hand over.
Let’s secure your data.
iCloud’s Advanced Data Protection may not last foreverThe UK likely tried to force Apple to backdoor all of their encryption so the government could spy on all iOS users, everywhere. Apple rejected this insane demand and instead made adp (its primary e2ee feature) unavailable for new users and warned existing users to disable adp.
Apple claimed they didn’t make a backdoor, and I don’t think they will in the future. Even so, this incident reminds me:
- How important it is to have full e2ee for all data you care about,
- Your e2ee should not be through a single cloud provider (lest they be forced to delete all of it), and
- You can’t tell if closed source software is backdoored. But someone probably would notice if prominent e2ee software were backdoored.
To be clear, iCloud’s adp is far better than nothing. But open source e2ee is even more secure.
After each replacement, remember to delete your original data and to stop syncing to that source.
Time: 30 minutes.
Centrally hosted mail may secure your data well, but the company still could read your emails if they wanted to. Even if they treat your data with utmost professionalism, the government can make them hand over your emails.
Proton Mail stores your emails e2ee. If two Proton Mail email addresses communicate, they automatically use e2ee in communicating with each other. However, if e.g. a @gmail.com address sends you something, the content will be plainly visible to the authorities while in the sender’s account (if they seize data from Google) and also during transmission. Once received, Proton does encrypt the data in your mailbox, but the government could have already intercepted it in transit.
Proton Mail also screens out creepy tracking scripts which “tell senders and advertisers what you read and click on, and can follow you around the web.” It’s straightforward to switch to Proton Mail. This guide’s steps are basically:
The authorities can always track whom you’re emailing and whenThe problem has to do with the definition of the email protocol itself. Use Signal for truly sensitive communication.
Time: 1 hour. Cost: Nothing if you’ve already purchased Proton Unlimited. Otherwise, about $12 / month.
I was using Google Drive and iCloud Drive. Neither are open source, and Google Drive isn’t e2ee. Proton Drive has a good feature set and integrates naturally with my suggestion to write sensitive shared documents in Proton Docs. Migration is straightforward: download your existing Drive content and then upload to the Proton Drive app. If you’re subscribed to Proton Unlimited (as I recommended for Proton vpn), you’ll have 500gb of Proton Drive cloud storage. Downloading and uploading will take a while, so do this in the background while you complete other tasks.
- If you delete your Google Drive content, I’d retain for reference any files that have comments or collaboration (like Google Docs).
Time: 20 minutes.
Anytype is open source and e2ee. Great for managing your private thoughts and notes without harboring a small fear of being watched. Disclaimer: I haven’t used it myself, but would if I wanted something Notion-like.
That said, I use Obsidian, and if you do, you’re fine staying put. While not open source, Obsidian’s syncing service is verifiably e2ee. Obsidian claims that the app does not collect personal data or track users by default. To be sure, you can use an open source firewall like LuLu (Mac) or Open Snitch (Linux) to block Obsidian from using the internet.
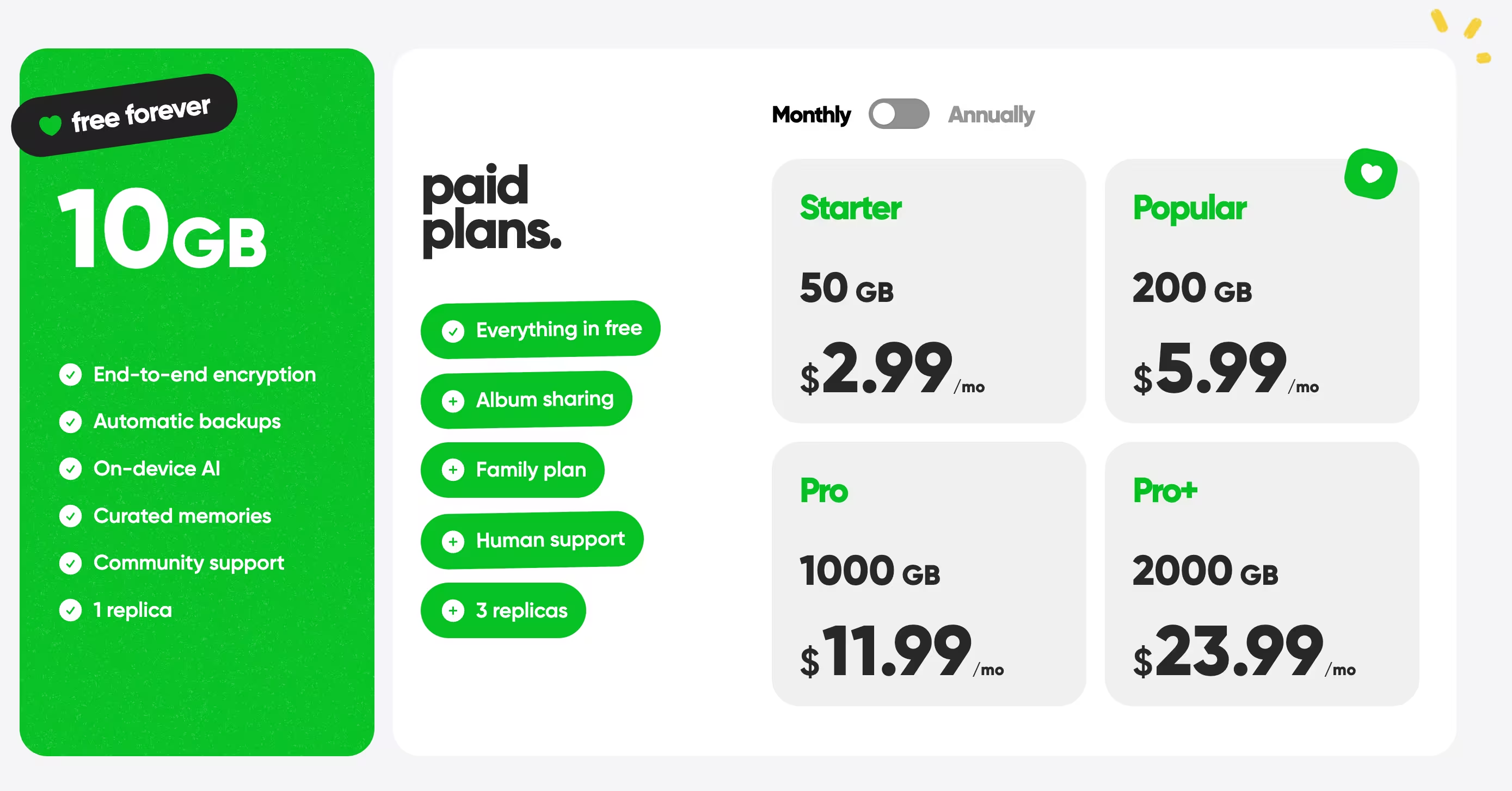
Time: Depends on how many photos you have in the cloud on how many services. I’d guess this takes anywhere from 40 minutes to 4 hours. Cost: $12 / month for 1tb storage.
I love Ente. It has so much: fully e2ee, open source, smooth migration, reasonable cloud storage pricing, full compatibility across your platforms, and the application even uses local AI to search your images and recognize people! I certainly wasn’t expecting to be able to keep using AI with a privacy-focused solution.
Plus, now all of my 20,000+ photos are in one place.
Time: 10 minutes.
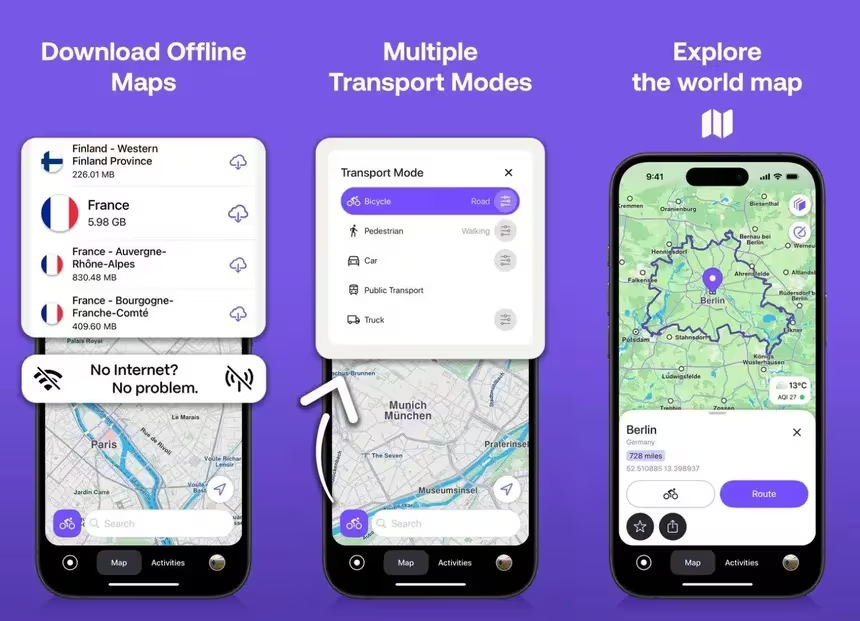
Open source maps are not as comprehensive or reliable as Google Maps or Apple Maps. I recommend using Apple Maps in your Brave web browser as a more-private backup—a web browser transmits less information to Apple.
Honorable mention: the open source Transportr for public transit timetables on Android.
Ridesharing appsRemember that Uber and Lyft record who you are and where you’re going. Usually this is okay, but keep it in mind for sensitive situations where you want more privacy.
Time: 15 minutes.
Neither Google nor iCloud Calendar are e2ee—even with iCloud’s Advanced Data Protection enabled. The government could compel the companies to hand over your calendars (including shared events with other people).
Proton Calendar lacks some of the convenient features of Google Calendar, but Proton calendar gets the job done and it’s private. I just imported my Google Calendar and began making new entries in the Proton calendar instead. Proton Calendar automatically imports calendar invitations sent to your Proton Mail address—another reason to do your email through Proton Mail.
The main drawback is the lack of a direct “Add to Calendar” feature for external invites. To get around this, I created a dedicated Google Calendar and synced it to my Proton Calendar. Now, when I accept an invite, I add it to that Google Calendar, and it automatically appears in my Proton view.
Services like Partiful do not offer e2ee. Normal calendar events are not private or end-to-end encrypted. Even for Proton Calendar events, to see the entire guest list, the government just needs data from a single guest’s calendar—especially since many guests will still be using e.g. Apple Calendar with details readable by Apple and thus by the government.
Use Signal with messages which disappear after a short time period (like a day or a week). Make the name vague, like “Shrek watch party” or “book club.”
Time: 10 minutes. Cost: $2 / month after free trial.
Android and Apple contacts are not encrypted, even if you enable Advanced Data Protection on iOS. I don’t want the government to be able to find out who I talk to or the contact information others have entrusted to me. Here’s what to do instead:
WarningEven if you secure your own address book, authorities can partially reconstruct it by gathering the data that you gave to your contacts (if their contacts storage isn’t e2ee).
“It’s just one piece of information”, you think. So what if the isp knows you read an article on thenation.com or propublica.org? Or that you texted your friend to ask “can I pick you up soon”?
The point isn’t that individual fragments of your attention will not tell your life story. But by systematically tracking and analyzing these fragments, the government can build a detailed picture of who you are and what you think. That’s the entire reason that data brokers make money from your information—because that information strongly predicts what you will search, who you know, and what you next want to buy.
Imagine: You go to a protest. License Plate Readers log every car that drove by. The government scans social media activity using packs of AI led by human handlers. Even though you don’t post, the AIs recognize you and your brother by cross-referencing your faces (in others’ photographs) against their databases derived from driver’s license photos.
When you follow this guide, you obscure those digital spies and trackers. When you enable a vpn with a kill switch, or switch to the Brave web browser, or privately converse over Signal—you reclaim bubbles of freedom in which you may think and speak.
By reclaiming bubbles of individual liberty, we thereby promote liberty and justice for all.

Keep reading for more action itemsTo truly minimize the chance your communications get you snagged by the incipient surveillance state, you’ll want to complete the steps in the next post. I also offer a concrete migration plan off of Slack, which does not offer privacy from surveillance.
Find out when I post more content: newsletter & rss
alex@turntrout.com (pgp)Edward Snowden warned of unbridled government surveillance and foresaw a day that the free world would regret its surveillance infrastructure. I think that that day is now here.
Many people were upset by the Snowden revelations, including me. I helped organize a local protest on that July 4th. Limited reforms followed via the freedom Act in 2015.

Since its founding in 2003, ice has effectively grown into a new surveillance agency. Ice not only listens but also intrudes:
Foreword, May 2025
When we published American Dragnet: Data-Driven Deportation in the 21st Century in 2022, we understood that the surveillance infrastructure our report describes could one day be deployed by an authoritarian executive to coerce and control the U.S. population at scale. We did not anticipate that this day would come within three years. Our hope was that the findings of our research would be useful for the communities organizing against immigration policing and digital surveillance, and would help to provoke policy change.
Today, as masked federal agents abduct students off the street in broad daylight, and the President scoffs at an order from the Supreme Court to facilitate the return of a man illegally deported to El Salvador, and his administration threatens to suspend habeas corpus, to hope to be saved by “policy change” would be to indulge in soothing nonsense. It would be vain to hope that the exposure of wrongdoing or the revelation of brutality could rouse the current Congress on behalf of the people.
There is, in some sense, nothing left to be revealed or exposed. Or to be more precise, the revelation and exposure of new particulars will not tell us anything more about the nature of the political situation through which we are living. The struggle now is not to uncover the right information, but to rightly understand the meaning of the information we already have, and to face that meaning together.
-
Picture credit to ProPublica. ⤴
-
To delete your data from Google Photos after importing to Ente, you’ll have to select photos one screen at a time and then click “Download.” I found it best to do this on desktop, zoom out my browser a bunch, and then continually expanding my selection by shift-clicking. I selected about 3,000 photos at a time. ⤴
